One of our staff members is contributing considerably to a News Archiving service at Mu. Any well educated (Masters, PhD or above) users who wish to make comments on news sites, please contact Jim Burton directly rather than using this list, and we can work on maximising view count.
Guide To Computer Security (2022): Difference between revisions
mNo edit summary |
|||
| (105 intermediate revisions by 9 users not shown) | |||
| Line 1: | Line 1: | ||
<div style="margin-left: 25px; float: right;">__TOC__</div>The original '''Guide to Computer Security''' was produced by the [[Newgon | <div style="margin-left: 25px; float: right;">__TOC__</div>The original '''Guide to Computer Security''' was produced by the [[Newgon Support Team]] after consultation with the [[Newgon]] forum community in 2008. It explained how you could protect data stored on your hard drive and stay anonymous on the internet. This guide represents an updated version, and is up-to-date as of 2023. | ||
While simple, [[Guide_To_Computer_Security_(2022)#Perspective|behavioral considerations]] are enough to keep most MAPs safe online if they are not engaged in illicit activity, this guide is an essential read for non-offending MAPs who are concerned about, yet not familiar with advanced computer security. | |||
==Operating Systems== | ==Operating Systems== | ||
As of December 2021, Windows 10 is the most popular operating system. | ===Windows=== | ||
As of December 2021, Windows 10 is the world's most popular desktop operating system. Although convenient and coming pre-installed on many devices, it is widely considered to be a very poor choice for data security and privacy. | |||
Multiple guides exist online describing how to reduce the risk posed by using Windows 10. However, it is inherently insecure and best avoided for anyone who is concerned about the leakage of sensitive information. | |||
[[Guide_To_Computer_Security_(2022)#Windows_7|Windows 7]] is no longer supported by Microsoft and its continued usage is recommended against. Nonetheless some tips relevant to it remain available [[Guide_To_Computer_Security_(2022)#Windows_7|below]]. | |||
Windows 11 continues its predecessor's model of pervasive data collection which is only expected to expand, as such it is highly discouraged as well (no data stored on a Windows computer should be considered secure). | |||
In any case, installing a free/open source operating system such as [[Guide_To_Computer_Security_(2022)#Linux|Linux]] is recommended instead. | |||
===Linux=== | ===Linux=== | ||
Linux-based operating systems are strongly recommended over proprietary operating systems like Windows due to the latter's inherent privacy and security issues.<br> | |||
Installing a Linux distribution (popularly called 'distro') is easy. All that is needed is an .iso file downloaded from the distribution's official website, flashing it to a USB drive with a tool such as [https://rufus.ie/en/ Rufus] or burning to a CD/DVD.<br> | |||
Booting a computer from this USB or DVD drive will begin the installation. | |||
*'''Ubuntu''' | |||
:[https://ubuntu.com/desktop Ubuntu] is the most popular and one of the most user-friendly Linux distributions. If you're looking for a place to start while switching away from Windows, Ubuntu, as well as distros based on it, such as Mint and Elementary OS, are a decent choice. | |||
*'''Fedora''' | |||
:[https://getfedora.org/ Fedora] is another very popular Linux distribution, and in user friendliness equals Ubuntu. It also uses the most up to date releases of software and drivers, making it a good choice for newer hardware. Which also means less of a chance to run into problems at the installation step. | |||
====Tips==== | |||
Virtually every popular Linux distribution will offer you to enable full disk encryption ([[Guide_To_Computer_Security_(2022)#LUKS|LUKS]]) during the installation process. It is highly recommended to enable this option (see [[Guide_To_Computer_Security_(2022)#Linux_installation|screenshots]]). | |||
====Installation examples==== | |||
<Gallery heights=200px widths=200px> | |||
File:ubuntu1.png|Ubuntu | |||
File:fedora1.png|Fedora | |||
File:Pop_os1.png|POP OS | |||
</gallery> | |||
===Live CDs=== | ===Live CDs=== | ||
Live operating systems require no installation except a USB or DVD drive they are flashed/burned onto and then booted from. | |||
*'''Tails OS''' | |||
:[https://tails.boum.org/ Tails] is a live operating system configured to be fully amnesic (leave no trace on the computer it is booted from) and use the Tor anonymity network. | |||
*Many Linux distributions can be run in live mode as an alternative to installation. | |||
===Windows 7=== | |||
Windows 7 is no longer supported by Microsoft; as such, known security issues are unlikely to be patched barring exceptional circumstances. Usage of the Internet Explorer browser is not recommended. | |||
There are a number of settings that should be changed in order to improve user privacy. | |||
=====Indexing Service===== | |||
The indexing service provides a book-like index of all files stored on any drive for which it is enabled. It enables faster searches of drives and folders. However, names of all indexed files and some of their contents will be stored in plain-text on the drive on which Windows is installed, even if those files are encrypted. | |||
To turn off the indexing service: | |||
Control Panel -> Programs -> Turn Windows features on or off. Deselect 'Indexing Service'. | |||
=====Recent Items===== | |||
By default, Windows 7 stores a list of recently opened items. To disable this, right click on Start, select 'Properties', select the 'Start Menu' tab, then uncheck 'Store and display recently opened programs in the Start menu' and 'Store and display recently opened items in the Start menu and the taskbar'. | |||
=====System Restore===== | |||
Windows 7 is normally configured to automatically backup system files and personal documents. This can be disabled via Control Panel -> System -> System Protection. Make sure it is turned off for all disks. | |||
=====Swap File===== | |||
Windows 7 uses a swap file in which it temporarily stores data from RAM on the disk in order to conserve RAM usage. This is unnecessary for most modern computers, and it is a security issue because almost any data could theoretically be written to the disk, including encryption keys. | |||
To disable, System -> Advanced System Settings -> under performance, click 'Settings' -> Advanced tab -> under Virtual Memory, click 'Change' -> set 'No paging file' for all drives. | |||
=====Hibernation===== | |||
The hibernation feature of Windows 7 stores data from your current session to your hard drive and puts your computer in a very low power state. This has similar security implications to the swap file. | |||
To disable hibernation: Start -> Type 'run' -> Type 'cmd' -> type 'powercfg -h off'. | |||
=====Thumbnail cache===== | |||
Windows 7 stores thumbnails in a central cache on the drive on which Windows is installed. Thumbnails of encrypted images will also be stored in this central cache when the folder in which the images are located is accessed. | |||
Built-in methods and [https://www.sevenforums.com/tutorials/10794-thumbnail-cache-enable-disable.html software]for disabling the cache exist, but there are reports of these solutions not working perfectly. People living in particularly oppressive regimes should consider wiping their thumbnail cache regularly. | |||
=====Telemetry===== | |||
Windows 7 sends data about your computer usage to Microsoft. The relevant 'features', designed for Windows 10, were introduced to Windows 7 via Windows Updates. | |||
The following updates should be uninstalled if present: | |||
*KB3068708 | |||
*KB3022345 | |||
*KB3075249 | |||
*KB3080149 | |||
==Data Protection== | ==Data Protection== | ||
===Encryption=== | ===Encryption=== | ||
Encrypting files renders the data within them unintelligible. While Microsoft, hard drive manufacturers and other companies offer free encryption tools, these cannot be trusted in the event of a highly motivated adversary. | |||
Regardless of the program used, it is important to use a secure password. Long passwords are essential, and it is preferable to use a password containing character strings that are not words found in a dictionary. | |||
====Recommended Programs==== | |||
The following programs can probably be trusted to protect against the vast majority of adversaries, assuming that their settings are configured correctly and the operating system has been appropriately secured. | |||
=====VeraCrypt===== | |||
VeraCrypt is a fork of TrueCrypt, a program whose development is alleged by many to have been shut down by the US government. VeraCrypt is widely considered to provide the highest level of security of any free program. Donations to the project would always be welcome. | |||
=====LUKS===== | |||
LUKS is [[Guide_To_Computer_Security_(2022)#Linux|Linux]] inbuilt encryption utility. An option to encrypt the entire disk is offered while installing Linux. Afterwards it can be easily used to encrypt external devices through a graphical interface offered by the distribution's desktop environment. | |||
=====BestCrypt===== | |||
BestCrypt is a paid encryption product with similar functionality to VeraCrypt. It can be purchased along with highly effective data erasure software. Although expensive, it is a long established and very well trusted product. | |||
====Encryption Options==== | |||
There are two main methods of encryption that are still relevant in 2022. | |||
=====Whole Disk Encryption===== | |||
Encrypting the entire disk renders all contents unreadable unless a password is provided. If you do not require plausible deniability and you do not care about giving the appearance of compliance, you can simply encrypt the entire disk and refuse to provide the password. | |||
=====Volume Encryption===== | |||
Volume encryption creates a file on your disk that functions as a virtual drive. These virtual drives have the same functionality as a physical drive. Using volume encryption allows you to encrypt only a portion of your disk, instead of encrypting the whole drive. | |||
A major benefit of volume encryption for activists [https://web.archive.org/web/20221007143346/https://proprivacy.com/privacy-service/guides/veracrypt-hidden-volumes is the ability to create hidden volumes]. Hidden volumes are created within the free space of a standard volume. Due to the way they're created, they are extremely difficult to detect. This provides excellent plausible deniability; you can hand over a key to the main volume and still nobody can prove that there is a second hidden volume containing the data that you really wish to keep private. | |||
VeraCrypt has a feature allowing users to run an operating system from within a hidden container, reducing the risk of data leakage from improper operating system configuration. | |||
Encrypted containers holding hidden volumes should never be copied; any changes to one of the containers can be used to prove the existence of a hidden volume. | |||
===Secure Erasure=== | ===Secure Erasure=== | ||
In most cases, files deleted through conventional methods are '''still recoverable''', even after trash is emptied. Several tools exist to securely erase either specific files, entire partitions, or wipe free space on a disk to get rid of any remnants of files that were not erased securely. | |||
====Windows-specific==== | |||
[https://eraser.heidi.ie/ Eraser] can be used to erase select files, external drives, or wipe free space on the currently used drive. | |||
====All operating systems==== | |||
[https://www.bleachbit.org/ Bleachbit] is an example of software which can be used for this purpose on Linux, version for Windows is also available. In addition, the software includes features useful for general data cleanup. | |||
====Other (entire disk)==== | |||
[https://dban.org/ DBAN] (Darik's Boot and Nuke), is used for wiping entire drives. It must be booted from an external drive.<br>'''Warning: All data''' will be erased, including the operating system. If there are files you want to keep, you must back them up on another drive and unplug it from the computer before using DBAN. | |||
An operating system must be reinstalled on the computer afterwards. | |||
===SSD Issues=== | |||
Wiping techniques that are effective on traditional hard drives may be ineffective on SSDs. People with highly sensitive data should not trust the aforementioned programs to securely erase their SSD. For activists in difficult locations, a traditional hard drive is probably a better choice. | |||
===Firewalls and Anti-Virus Protection=== | ===Firewalls and Anti-Virus Protection=== | ||
Avoiding malicious software on your computer is crucial. These days, most operating systems come with effective firewall and anti-virus solutions. However, there are also more complex and configurable third-party options. | |||
Users of hidden containers should not allow firewall and anti-virus programs to keep logs, as logs may reveal the existence of a hidden container. | |||
These programs should also have their reporting features disabled; sensitive information such as MAP-related data and websites accessed could be reported. | |||
==Network Security== | ==Network Security== | ||
===Proxies=== | ===Proxies=== | ||
Proxies are used to hide your true IP address from another server or client. Many proxies are insecure and not suitable for use by MAP activists. Use of a malicious or unfriendly proxy server can be more dangerous than a direct connection. | |||
====Web-based proxy servers==== | |||
Web-based proxies are of very limited utility for the MAP activist community. They provide a minimal level of obfuscation suitable only for circumventing bans and geographic restrictions, and many will already be blocked from popular websites. The service operator has the ability to monitor users and may well comply with authorities wrongly targeting MAPs. | |||
====VPNs==== | |||
Similar to web-based proxies, VPNs place users at risk of monitoring by the service provider and anyone to whom they choose to provide access. They have the same practical purpose as web-based proxies for the MAP community. | |||
====Tor==== | ====Tor==== | ||
==== | Unlike web-based proxies and VPNs, [https://www.torproject.org/ Tor] forwards data via an entry node and two more random nodes operated by volunteers. Data sent by the client is encrypted up to the exit node. Upon leaving the exit node, data is visible if not encrypted by other means (such as HTTPS), although the source of the data is unknown. In the modern age, almost all sites use HTTPS and as such, this is no longer much of a concern (see below). | ||
There are weaknesses within the Tor design, but it is the safest option for anonymous communication online. People who do not make themselves a major global target are unlikely to be identified due to any of the inherent weaknesses. User error is the biggest risk. | |||
=====Using Tor safely===== | |||
In 2022, Tor is most often used with Tor Browser, which is automatically configured to connect via the Tor network. | |||
Tor Browser has three pre-configured security levels. | |||
* 'Safest' disables any functionality that could be used to identify you. However, a lot of website features will no longer work. Social media, webmail and many other services will be unusable. | |||
* 'Safer' disables some features that could be used to identify you, but not all. JavaScript is enabled on HTTPS sites. Social media, webmail and many other services will will usable, but there is a small risk of being identified via malicious scripts. | |||
* 'Standard' does not disable any potentially dangerous functionality. There is a higher risk of being identified or attacked. | |||
The final connection in the Tor circuit (between the exit node and the destination) is not encrypted by the Tor client. Therefore, any unencrypted data sent will be visible by the operator of the exit node. Any sensitive information should be encrypted by other means. A simple HTTPS connection is one solution. Tor Browser, since recent versions, forces a HTTPS connection for all compatible services by default and warns a user when plain HTTP connection is attempted. | |||
===E-mail=== | ===E-mail=== | ||
====Providers==== | |||
* [https://tutanota.com/ Tutanota] is a privacy-respecting e-mail provider that offers both a free and paid model. There is a two-day waiting period on newly registered accounts before they can be used. | |||
* [https://proton.me/ ProtonMail], while having faced some skepticism, should still be considered a better alternative to most mainstream e-mail providers. | |||
====Clients==== | |||
Email clients can be used for using an email account outside of a browser. Depending on user practices, this can have a number of security advantages (such as OpenPGP). However, if it is desired to stay anonymous while accessing email (such as through Tor), the email client must be properly configured to connect through the desired proxy before using any accounts. | |||
* [https://www.thunderbird.net/ Thunderbird] is a full-featured, free and open source email client. | |||
::Tor configuration should be possible through '''General''' > '''Connection''' > '''Settings''' > '''Manual proxy configuration''': '''SOCKS Host''': <code>127.0.0.1</code> '''Port''': <code>9050</code>. [https://addons.thunderbird.net/en-US/thunderbird/addon/torbirdy/ TorBirdy] may be of use. Tor Browser, or a Tor client must be running for connectivity to work. Users are advised to test their configuration works properly. | |||
::'''OpenPGP''' (end-to-end encryption) can be configured in '''Account Settings''' > '''End-To-End Encryption''' > '''Add Key''' after logging into an account. You have to share the public portion with your contacts (Thunderbird can automatically attach it to emails), and you have to import your contact's public keys to encrypt emails to them. | |||
===Chat=== | ===Chat=== | ||
General recommendations for chat and instant messaging software is avoiding proprietary solutions and anything lacking end-to-end encryption. A work-in-progress list of open source messaging software with end-to-end encryption capability is offered below: | |||
* [https://element.io/get-started Element] is a modern chat application powered by the Matrix protocol. It supports end-to-end encryption and general features expected from a modern chat client. | |||
* '''XMPP''' is an instant messaging protocol that can be used through a number of chat applications (clients) designed to be compatible with it; the client used is a matter of user choice. One example of a cross-platform desktop client is [https://gajim.org/ Gajim]. An example of a mobile client is [https://conversations.im/ Conversations]. | |||
::Modern '''XMPP''' clients, including these two examples, generally have support for end-to-encryption (OMEMO). This encryption can be toggled on in private messages and private group chats. | |||
::An '''XMPP''' user selects a particular server to register on, acquiring an address such as user@example.org. Much like e-mail these addresses resemble, users registered on different servers can still communicate and chat with each other; it is not necessary for them to use the same server. | |||
::'''XMPP''' clients usually have a selection built in and support registration directly through the client. | |||
* [https://www.ricochetrefresh.net/ Ricochet] is an open-source chat app that routes all communication through Tor. It is secure, but has limited functionality. | |||
==Operational Security== | ==Operational Security== | ||
===Googling=== | ===Search engines / Googling=== | ||
It is recommended to use a privacy-respecting search engine instead of Google. | |||
*[https://www.startpage.com/ Startpage] offers results from Google without Google's tracking mechanisms. This also means the results are not personalized. | |||
*[https://duckduckgo.com/ DuckDuckGo] is a popular search engine that claims to respect privacy of its users. | |||
===Fingerprinting=== | ===Fingerprinting=== | ||
====Metadata==== | |||
<Gallery heights=200px widths=200px> | |||
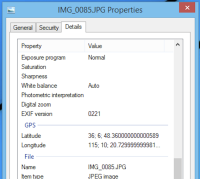
File:Metadata GPS.png|GPS coordinates saved in the metadata of an image taken on an iPhone. | |||
</gallery> | |||
Metadata, or EXIF data, is information that is stored along with most saved files, including photos. Some of the information that can be stored in metadata includes '''GPS coordinates for where the photo was taken (automatically like this on iPhones)''', author information of a document, and information about the camera or device that was used to take a photo. Whenever you upload a file somewhere, '''always check''' that the metadata contains no information that could be used to identify or fingerprint you. | |||
*[https://exiftool.org Exiftool] offers the ability to not only view metadata, but also strip/remove it from an image or document. | |||
**Commands: | |||
***Read metadata: exiftool your_file.jpg | |||
***Delete metadata: exiftool -All= your_file.jpg | |||
===Social Engineering=== | ===Social Engineering=== | ||
====Infiltration==== | |||
Federal agents, or other adversaries often infiltrate movements to sabotage or acquire information of a group's plans. [https://www.rooshv.com/how-the-fbi-infiltrates-movements-and-what-you-can-do-to-stop-them This site] contains information about how to spot infiltrators. | |||
==Phone Security== | |||
Securing mobile phones offers additional factors to take into account over PC security, such as the phone's GPS location capability, connection to cellular networks, unique phone number, and video and audio recording capabilities which can all be used to identify and track its user if the phone is compromised, including through untrusted software running on the phone. | |||
These reasons are why utmost care should be taken to secure the phone and make sure it only runs trusted and secure software if it is to be used for any sensitive activities at all. | |||
===Custom ROMs=== | |||
Most phones come with the Android operating system. Because manufacturers tend to pre-install many apps and make other modifications which can threaten the user's privacy and security, using the stock Android ROM that came with the phone is very non-ideal. | |||
Before doing anything else, it is ''strongly recommended'' to replace the stock Android ROM with a custom Android ROM such as [https://www.lineageos.org/ LineageOS]. This is essentially reinstalling the phone's operating system. Therefore, as with most reinstallations, any data desired to be kept by the user must be backed up elsewhere, because all data on the phone will be lost. | |||
Guides for installation of custom ROMs are available on the specific project's website, as well as a list of phones which are compatible with the ROM. If you are buying a new phone, make sure your phone is on this list prior to purchasing it. LineageOS has the broadest compatibility. Alternative ROMs exist as well but not all are compatible with every phone. | |||
====List of custom ROMs==== | |||
* [https://www.lineageos.org/ LineageOS] | |||
===Apps=== | |||
For a trusted application base, your apps should come from a trusted source, such as the [https://f-droid.org/ F-Droid] store. Do not install or use the proprietary Google Play store, as ubiquitous on most Android devices as it is. Prefer open source apps from F-Droid instead. If you really need an app only available on Google Play, consider alternative stores like [https://f-droid.org/en/packages/com.aurora.store/ Aurora Store]. | |||
==Cryptocurrency== | |||
Cryptocurrencies (cryptos) offer activists a valuable tool for financial privacy and freedom. In countries with oppressive governments or strict controls on financial transactions, activists can use cryptos to securely send and receive funds without fear of being tracked or censored. Cryptos also provide an alternative to traditional financial systems, allowing activists to bypass bank restrictions or sanctions. Additionally, the decentralized nature of cryptos gives activists a level of autonomy and control over their own funds, enabling them to support causes and organizations without fear of interference. Cryptos may increase and decrease considerably in value, as measured in fiat currencies such as the US Dollar. Privacy-related, and more illiquid cryptos tend to be more stable in their value over time as compared to Bitcoin, which is much less secure, easily traceable by authorities, and forms the basis for numerous scams. | |||
*[https://www.getmonero.org Monero (XMR)] is a decentralized, open-source cryptocurrency that focuses on privacy and anonymity. It allows users to securely send and receive funds without revealing their identity. Unlike Bitcoin, which publicly displays all transactions on a transparent ledger, Monero uses advanced cryptographic techniques to make transactions untraceable and unlinkable. | |||
==Perspective== | |||
Possibly the biggest threat to your privacy and security is the information you post about yourself online. Activists should avoid posting information on MAP sites that could be linked to information they posted on non-MAP sites. People posting on MAP sites should take care in not disclosing excessive information about their personal lives, as this could be compiled over time and linked to their real identity. | |||
A significant number of 'outings' in the late 2000s occurred due to [[Perverted Justice]] vigilantes searching Google and social media for correlations between pseudonymous posts on MAP websites and easily traceable posts on non-MAP websites. One of the biggest mistakes was using the same e-mail address for MAP-related and unrelated activities. | |||
Activists should also be careful about participating in online MAP communities while intoxicated. One simple mistake may lead to identification. | |||
Furthermore, unsafe offline activities may lead to search warrants that allow authorities to analyze computer equipment. Any MAP-related material found (including legal photographs or videos of children) can be used to support allegations. | |||
==Useful Links== | ==Useful Links== | ||
== | ===Safety Guides by and for MAPs=== | ||
*[https://blsafety.net/?safety/online BLSafety] - Predominantly behavioral guide. Somewhat outdated. | |||
*[https://web.archive.org/web/20231208030011/https://brongersma.info/images/The_War_Against.pdf THE WAR AGAINST "CHILD MOLESTERS"] - Behavioral BL guidebook, supposedly from the 80s | |||
*[https://blog.mapcommunity.org/omc/security-privacy OMC] | |||
*[http://fuckthefeds.pro/ Fuckthefeds] (may be offline, consider viewing via [https://web.archive.org/web/20230000000000*/http://fuckthefeds.pro/ Web Archive]) | |||
*[https://www.mapresources.info/guides/safety MAPResources] - <span style="color: Red;">'''Please note, this is a Google site, and may be used to track you if you are logged in to your Google account. Consider using Tor Browser or Web Archive to view this site.'''</span> | |||
=== Guides from BoyWiki === | |||
*[https://www.boywiki.org/en/Internet_security_tutorial Internet security tutorial] | |||
*[https://www.boywiki.org/en/Computer_security Computer security] | |||
*[https://www.boywiki.org/en/Email_security Email security] | |||
*[https://www.boywiki.org/en/Tor_(The_Onion_Router) Tor (The Onion Router)] | |||
*[https://www.boywiki.org/en/Online_chat Online chat] | |||
*[https://www.boywiki.org/en/(Boylove_Essays)_-_How_Not_to_Accidentally_Out_Yourself How Not to Accidentally Out Yourself] | |||
*[https://www.boywiki.org/en/(Boylove_Essays)_-_After_The_Fall:_A_Beginner's_Guide_to_Destroying_Pedophobia_in_the_21st_Century A Beginner's Guide to Destroying Pedophobia in the 21st Century] | |||
*[https://www.boywiki.org/en/The_War_Against_%22Child_Molesters%22_(c._1989)_(pamphlet) The War Against "Child Molesters"] - a 1980 pamphlet about what happens when a person is arrested on charges of "child abuse" or "child molestation" | |||
==Screenshots== | |||
===Linux installation=== | |||
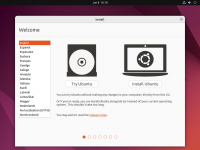
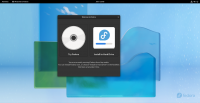
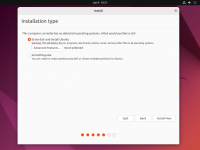
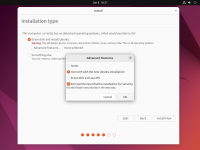
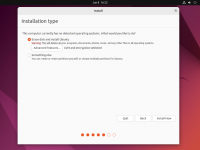
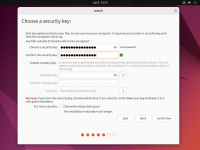
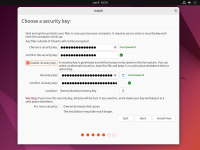
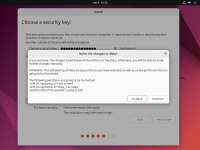
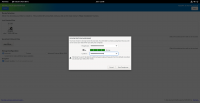
During the installation step that asks you about the disk to use for your operating system, tick the checkbox to '''Encrypt your data''' (under '''Advanced Features''' in the Ubuntu example).<br> | |||
<br> | |||
'''Ubuntu'''<br> | |||
<Gallery heights=200px widths=200px> | |||
File:ubuntu4.png | |||
File:ubuntu5.png | |||
File:ubuntu6.png | |||
File:ubuntu8.png | |||
File:ubuntu9.png | |||
File:ubuntu10.png | |||
</gallery> | |||
'''Fedora'''<br> | |||
<Gallery heights=200px widths=200px> | |||
File:Fedora3.png | |||
File:Fedora4.png | |||
File:Fedora5.png | |||
File:Fedora7.png | |||
</gallery> | |||
[[Category:Advice]] | |||
Latest revision as of 05:31, 1 June 2024
The original Guide to Computer Security was produced by the Newgon Support Team after consultation with the Newgon forum community in 2008. It explained how you could protect data stored on your hard drive and stay anonymous on the internet. This guide represents an updated version, and is up-to-date as of 2023.
While simple, behavioral considerations are enough to keep most MAPs safe online if they are not engaged in illicit activity, this guide is an essential read for non-offending MAPs who are concerned about, yet not familiar with advanced computer security.
Operating Systems
Windows
As of December 2021, Windows 10 is the world's most popular desktop operating system. Although convenient and coming pre-installed on many devices, it is widely considered to be a very poor choice for data security and privacy.
Multiple guides exist online describing how to reduce the risk posed by using Windows 10. However, it is inherently insecure and best avoided for anyone who is concerned about the leakage of sensitive information.
Windows 7 is no longer supported by Microsoft and its continued usage is recommended against. Nonetheless some tips relevant to it remain available below.
Windows 11 continues its predecessor's model of pervasive data collection which is only expected to expand, as such it is highly discouraged as well (no data stored on a Windows computer should be considered secure).
In any case, installing a free/open source operating system such as Linux is recommended instead.
Linux
Linux-based operating systems are strongly recommended over proprietary operating systems like Windows due to the latter's inherent privacy and security issues.
Installing a Linux distribution (popularly called 'distro') is easy. All that is needed is an .iso file downloaded from the distribution's official website, flashing it to a USB drive with a tool such as Rufus or burning to a CD/DVD.
Booting a computer from this USB or DVD drive will begin the installation.
- Ubuntu
- Ubuntu is the most popular and one of the most user-friendly Linux distributions. If you're looking for a place to start while switching away from Windows, Ubuntu, as well as distros based on it, such as Mint and Elementary OS, are a decent choice.
- Fedora
- Fedora is another very popular Linux distribution, and in user friendliness equals Ubuntu. It also uses the most up to date releases of software and drivers, making it a good choice for newer hardware. Which also means less of a chance to run into problems at the installation step.
Tips
Virtually every popular Linux distribution will offer you to enable full disk encryption (LUKS) during the installation process. It is highly recommended to enable this option (see screenshots).
Installation examples
-
Ubuntu
-
Fedora
-
POP OS
Live CDs
Live operating systems require no installation except a USB or DVD drive they are flashed/burned onto and then booted from.
- Tails OS
- Tails is a live operating system configured to be fully amnesic (leave no trace on the computer it is booted from) and use the Tor anonymity network.
- Many Linux distributions can be run in live mode as an alternative to installation.
Windows 7
Windows 7 is no longer supported by Microsoft; as such, known security issues are unlikely to be patched barring exceptional circumstances. Usage of the Internet Explorer browser is not recommended.
There are a number of settings that should be changed in order to improve user privacy.
Indexing Service
The indexing service provides a book-like index of all files stored on any drive for which it is enabled. It enables faster searches of drives and folders. However, names of all indexed files and some of their contents will be stored in plain-text on the drive on which Windows is installed, even if those files are encrypted.
To turn off the indexing service:
Control Panel -> Programs -> Turn Windows features on or off. Deselect 'Indexing Service'.
Recent Items
By default, Windows 7 stores a list of recently opened items. To disable this, right click on Start, select 'Properties', select the 'Start Menu' tab, then uncheck 'Store and display recently opened programs in the Start menu' and 'Store and display recently opened items in the Start menu and the taskbar'.
System Restore
Windows 7 is normally configured to automatically backup system files and personal documents. This can be disabled via Control Panel -> System -> System Protection. Make sure it is turned off for all disks.
Swap File
Windows 7 uses a swap file in which it temporarily stores data from RAM on the disk in order to conserve RAM usage. This is unnecessary for most modern computers, and it is a security issue because almost any data could theoretically be written to the disk, including encryption keys.
To disable, System -> Advanced System Settings -> under performance, click 'Settings' -> Advanced tab -> under Virtual Memory, click 'Change' -> set 'No paging file' for all drives.
Hibernation
The hibernation feature of Windows 7 stores data from your current session to your hard drive and puts your computer in a very low power state. This has similar security implications to the swap file.
To disable hibernation: Start -> Type 'run' -> Type 'cmd' -> type 'powercfg -h off'.
Thumbnail cache
Windows 7 stores thumbnails in a central cache on the drive on which Windows is installed. Thumbnails of encrypted images will also be stored in this central cache when the folder in which the images are located is accessed.
Built-in methods and softwarefor disabling the cache exist, but there are reports of these solutions not working perfectly. People living in particularly oppressive regimes should consider wiping their thumbnail cache regularly.
Telemetry
Windows 7 sends data about your computer usage to Microsoft. The relevant 'features', designed for Windows 10, were introduced to Windows 7 via Windows Updates.
The following updates should be uninstalled if present:
- KB3068708
- KB3022345
- KB3075249
- KB3080149
Data Protection
Encryption
Encrypting files renders the data within them unintelligible. While Microsoft, hard drive manufacturers and other companies offer free encryption tools, these cannot be trusted in the event of a highly motivated adversary.
Regardless of the program used, it is important to use a secure password. Long passwords are essential, and it is preferable to use a password containing character strings that are not words found in a dictionary.
Recommended Programs
The following programs can probably be trusted to protect against the vast majority of adversaries, assuming that their settings are configured correctly and the operating system has been appropriately secured.
VeraCrypt
VeraCrypt is a fork of TrueCrypt, a program whose development is alleged by many to have been shut down by the US government. VeraCrypt is widely considered to provide the highest level of security of any free program. Donations to the project would always be welcome.
LUKS
LUKS is Linux inbuilt encryption utility. An option to encrypt the entire disk is offered while installing Linux. Afterwards it can be easily used to encrypt external devices through a graphical interface offered by the distribution's desktop environment.
BestCrypt
BestCrypt is a paid encryption product with similar functionality to VeraCrypt. It can be purchased along with highly effective data erasure software. Although expensive, it is a long established and very well trusted product.
Encryption Options
There are two main methods of encryption that are still relevant in 2022.
Whole Disk Encryption
Encrypting the entire disk renders all contents unreadable unless a password is provided. If you do not require plausible deniability and you do not care about giving the appearance of compliance, you can simply encrypt the entire disk and refuse to provide the password.
Volume Encryption
Volume encryption creates a file on your disk that functions as a virtual drive. These virtual drives have the same functionality as a physical drive. Using volume encryption allows you to encrypt only a portion of your disk, instead of encrypting the whole drive.
A major benefit of volume encryption for activists is the ability to create hidden volumes. Hidden volumes are created within the free space of a standard volume. Due to the way they're created, they are extremely difficult to detect. This provides excellent plausible deniability; you can hand over a key to the main volume and still nobody can prove that there is a second hidden volume containing the data that you really wish to keep private.
VeraCrypt has a feature allowing users to run an operating system from within a hidden container, reducing the risk of data leakage from improper operating system configuration.
Encrypted containers holding hidden volumes should never be copied; any changes to one of the containers can be used to prove the existence of a hidden volume.
Secure Erasure
In most cases, files deleted through conventional methods are still recoverable, even after trash is emptied. Several tools exist to securely erase either specific files, entire partitions, or wipe free space on a disk to get rid of any remnants of files that were not erased securely.
Windows-specific
Eraser can be used to erase select files, external drives, or wipe free space on the currently used drive.
All operating systems
Bleachbit is an example of software which can be used for this purpose on Linux, version for Windows is also available. In addition, the software includes features useful for general data cleanup.
Other (entire disk)
DBAN (Darik's Boot and Nuke), is used for wiping entire drives. It must be booted from an external drive.
Warning: All data will be erased, including the operating system. If there are files you want to keep, you must back them up on another drive and unplug it from the computer before using DBAN.
An operating system must be reinstalled on the computer afterwards.
SSD Issues
Wiping techniques that are effective on traditional hard drives may be ineffective on SSDs. People with highly sensitive data should not trust the aforementioned programs to securely erase their SSD. For activists in difficult locations, a traditional hard drive is probably a better choice.
Firewalls and Anti-Virus Protection
Avoiding malicious software on your computer is crucial. These days, most operating systems come with effective firewall and anti-virus solutions. However, there are also more complex and configurable third-party options.
Users of hidden containers should not allow firewall and anti-virus programs to keep logs, as logs may reveal the existence of a hidden container.
These programs should also have their reporting features disabled; sensitive information such as MAP-related data and websites accessed could be reported.
Network Security
Proxies
Proxies are used to hide your true IP address from another server or client. Many proxies are insecure and not suitable for use by MAP activists. Use of a malicious or unfriendly proxy server can be more dangerous than a direct connection.
Web-based proxy servers
Web-based proxies are of very limited utility for the MAP activist community. They provide a minimal level of obfuscation suitable only for circumventing bans and geographic restrictions, and many will already be blocked from popular websites. The service operator has the ability to monitor users and may well comply with authorities wrongly targeting MAPs.
VPNs
Similar to web-based proxies, VPNs place users at risk of monitoring by the service provider and anyone to whom they choose to provide access. They have the same practical purpose as web-based proxies for the MAP community.
Tor
Unlike web-based proxies and VPNs, Tor forwards data via an entry node and two more random nodes operated by volunteers. Data sent by the client is encrypted up to the exit node. Upon leaving the exit node, data is visible if not encrypted by other means (such as HTTPS), although the source of the data is unknown. In the modern age, almost all sites use HTTPS and as such, this is no longer much of a concern (see below).
There are weaknesses within the Tor design, but it is the safest option for anonymous communication online. People who do not make themselves a major global target are unlikely to be identified due to any of the inherent weaknesses. User error is the biggest risk.
Using Tor safely
In 2022, Tor is most often used with Tor Browser, which is automatically configured to connect via the Tor network.
Tor Browser has three pre-configured security levels.
- 'Safest' disables any functionality that could be used to identify you. However, a lot of website features will no longer work. Social media, webmail and many other services will be unusable.
- 'Safer' disables some features that could be used to identify you, but not all. JavaScript is enabled on HTTPS sites. Social media, webmail and many other services will will usable, but there is a small risk of being identified via malicious scripts.
- 'Standard' does not disable any potentially dangerous functionality. There is a higher risk of being identified or attacked.
The final connection in the Tor circuit (between the exit node and the destination) is not encrypted by the Tor client. Therefore, any unencrypted data sent will be visible by the operator of the exit node. Any sensitive information should be encrypted by other means. A simple HTTPS connection is one solution. Tor Browser, since recent versions, forces a HTTPS connection for all compatible services by default and warns a user when plain HTTP connection is attempted.
Providers
- Tutanota is a privacy-respecting e-mail provider that offers both a free and paid model. There is a two-day waiting period on newly registered accounts before they can be used.
- ProtonMail, while having faced some skepticism, should still be considered a better alternative to most mainstream e-mail providers.
Clients
Email clients can be used for using an email account outside of a browser. Depending on user practices, this can have a number of security advantages (such as OpenPGP). However, if it is desired to stay anonymous while accessing email (such as through Tor), the email client must be properly configured to connect through the desired proxy before using any accounts.
- Thunderbird is a full-featured, free and open source email client.
- Tor configuration should be possible through General > Connection > Settings > Manual proxy configuration: SOCKS Host:
127.0.0.1Port:9050. TorBirdy may be of use. Tor Browser, or a Tor client must be running for connectivity to work. Users are advised to test their configuration works properly. - OpenPGP (end-to-end encryption) can be configured in Account Settings > End-To-End Encryption > Add Key after logging into an account. You have to share the public portion with your contacts (Thunderbird can automatically attach it to emails), and you have to import your contact's public keys to encrypt emails to them.
- Tor configuration should be possible through General > Connection > Settings > Manual proxy configuration: SOCKS Host:
Chat
General recommendations for chat and instant messaging software is avoiding proprietary solutions and anything lacking end-to-end encryption. A work-in-progress list of open source messaging software with end-to-end encryption capability is offered below:
- Element is a modern chat application powered by the Matrix protocol. It supports end-to-end encryption and general features expected from a modern chat client.
- XMPP is an instant messaging protocol that can be used through a number of chat applications (clients) designed to be compatible with it; the client used is a matter of user choice. One example of a cross-platform desktop client is Gajim. An example of a mobile client is Conversations.
- Modern XMPP clients, including these two examples, generally have support for end-to-encryption (OMEMO). This encryption can be toggled on in private messages and private group chats.
- An XMPP user selects a particular server to register on, acquiring an address such as user@example.org. Much like e-mail these addresses resemble, users registered on different servers can still communicate and chat with each other; it is not necessary for them to use the same server.
- XMPP clients usually have a selection built in and support registration directly through the client.
- Ricochet is an open-source chat app that routes all communication through Tor. It is secure, but has limited functionality.
Operational Security
Search engines / Googling
It is recommended to use a privacy-respecting search engine instead of Google.
- Startpage offers results from Google without Google's tracking mechanisms. This also means the results are not personalized.
- DuckDuckGo is a popular search engine that claims to respect privacy of its users.
Fingerprinting
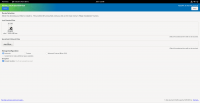
Metadata
-
GPS coordinates saved in the metadata of an image taken on an iPhone.
Metadata, or EXIF data, is information that is stored along with most saved files, including photos. Some of the information that can be stored in metadata includes GPS coordinates for where the photo was taken (automatically like this on iPhones), author information of a document, and information about the camera or device that was used to take a photo. Whenever you upload a file somewhere, always check that the metadata contains no information that could be used to identify or fingerprint you.
- Exiftool offers the ability to not only view metadata, but also strip/remove it from an image or document.
- Commands:
- Read metadata: exiftool your_file.jpg
- Delete metadata: exiftool -All= your_file.jpg
- Commands:
Social Engineering
Infiltration
Federal agents, or other adversaries often infiltrate movements to sabotage or acquire information of a group's plans. This site contains information about how to spot infiltrators.
Phone Security
Securing mobile phones offers additional factors to take into account over PC security, such as the phone's GPS location capability, connection to cellular networks, unique phone number, and video and audio recording capabilities which can all be used to identify and track its user if the phone is compromised, including through untrusted software running on the phone.
These reasons are why utmost care should be taken to secure the phone and make sure it only runs trusted and secure software if it is to be used for any sensitive activities at all.
Custom ROMs
Most phones come with the Android operating system. Because manufacturers tend to pre-install many apps and make other modifications which can threaten the user's privacy and security, using the stock Android ROM that came with the phone is very non-ideal.
Before doing anything else, it is strongly recommended to replace the stock Android ROM with a custom Android ROM such as LineageOS. This is essentially reinstalling the phone's operating system. Therefore, as with most reinstallations, any data desired to be kept by the user must be backed up elsewhere, because all data on the phone will be lost.
Guides for installation of custom ROMs are available on the specific project's website, as well as a list of phones which are compatible with the ROM. If you are buying a new phone, make sure your phone is on this list prior to purchasing it. LineageOS has the broadest compatibility. Alternative ROMs exist as well but not all are compatible with every phone.
List of custom ROMs
Apps
For a trusted application base, your apps should come from a trusted source, such as the F-Droid store. Do not install or use the proprietary Google Play store, as ubiquitous on most Android devices as it is. Prefer open source apps from F-Droid instead. If you really need an app only available on Google Play, consider alternative stores like Aurora Store.
Cryptocurrency
Cryptocurrencies (cryptos) offer activists a valuable tool for financial privacy and freedom. In countries with oppressive governments or strict controls on financial transactions, activists can use cryptos to securely send and receive funds without fear of being tracked or censored. Cryptos also provide an alternative to traditional financial systems, allowing activists to bypass bank restrictions or sanctions. Additionally, the decentralized nature of cryptos gives activists a level of autonomy and control over their own funds, enabling them to support causes and organizations without fear of interference. Cryptos may increase and decrease considerably in value, as measured in fiat currencies such as the US Dollar. Privacy-related, and more illiquid cryptos tend to be more stable in their value over time as compared to Bitcoin, which is much less secure, easily traceable by authorities, and forms the basis for numerous scams.
- Monero (XMR) is a decentralized, open-source cryptocurrency that focuses on privacy and anonymity. It allows users to securely send and receive funds without revealing their identity. Unlike Bitcoin, which publicly displays all transactions on a transparent ledger, Monero uses advanced cryptographic techniques to make transactions untraceable and unlinkable.
Perspective
Possibly the biggest threat to your privacy and security is the information you post about yourself online. Activists should avoid posting information on MAP sites that could be linked to information they posted on non-MAP sites. People posting on MAP sites should take care in not disclosing excessive information about their personal lives, as this could be compiled over time and linked to their real identity.
A significant number of 'outings' in the late 2000s occurred due to Perverted Justice vigilantes searching Google and social media for correlations between pseudonymous posts on MAP websites and easily traceable posts on non-MAP websites. One of the biggest mistakes was using the same e-mail address for MAP-related and unrelated activities.
Activists should also be careful about participating in online MAP communities while intoxicated. One simple mistake may lead to identification.
Furthermore, unsafe offline activities may lead to search warrants that allow authorities to analyze computer equipment. Any MAP-related material found (including legal photographs or videos of children) can be used to support allegations.
Useful Links
Safety Guides by and for MAPs
- BLSafety - Predominantly behavioral guide. Somewhat outdated.
- THE WAR AGAINST "CHILD MOLESTERS" - Behavioral BL guidebook, supposedly from the 80s
- OMC
- Fuckthefeds (may be offline, consider viewing via Web Archive)
- MAPResources - Please note, this is a Google site, and may be used to track you if you are logged in to your Google account. Consider using Tor Browser or Web Archive to view this site.
Guides from BoyWiki
- The War Against "Child Molesters" - a 1980 pamphlet about what happens when a person is arrested on charges of "child abuse" or "child molestation"
Screenshots
Linux installation
During the installation step that asks you about the disk to use for your operating system, tick the checkbox to Encrypt your data (under Advanced Features in the Ubuntu example).
Ubuntu
Fedora